Check out the new twitter design, looking great. This was my number-one complaint about twitter over the other micro-blogging services. It felt too myspace-ish, all that has changed.
Twitter Blog: Changes Afoot
Friday, September 19, 2008
Monday, September 8, 2008
Mobility, Part Two
In my previous article I spoke about Mobility. Having the ability to move freely and still have access to all of your data and services. More specifically I focused on Mobile devices and interfaces to our normally Desktop centric world. This time I will skim the surface of another form of Mobility: The Cloud.
Having the ability to go from one location/workstation to another, while still having access to your data, is an important hurdle to jump. Many business tackle this issue with "roaming profiles" and other shared resources. But what do you at home do when sharing a profile between, home, work, friends, and the library isn't an option? I'd assume you use an Application Service Provider.
Application Service Providers aren't any new concept, and Google is far from the first Company in invest time, money, and resources into the idea.
From Wikipedia: "In terms of their common goal of enabling customers to outsource specific computer applications so they can focus on their core competencies, ASPs may be regarded as the indirect descendants of the service bureaus of the 1960s and 1970s. In turn, those bureaus were trying to fulfill the vision of computing as a utility, which was first proposed by John McCarthy in a speech at MIT in 1961."
The idea is simple, you register for a service/application that is provided online. All of your information/data is stored on the providers servers. When you need to access the service/data you simple visit the website, and login, no matter your location.
I personally rely on cloud-based services as much as I rely on mobile applications. I have almost all of my email in Google's Gmail (either directly or through POP support or forwarding). I use the Google Calendar on a daily bases to help keep me on track, and update others of my whereabouts (when needed). Google Reader is a dream-come-true - one of the best readers available. Even this blog is an example of a Cloud based service I use. My list could continue, just as I am sure yours could. Even social-networks are a form of cloud computing.
I can easily go from my laptop at the airport, to the desktop at my house and never miss an article, re-read an email, or forget about an appointment. But better yet, when I am in an unfamiliar place (the library, public system, friends house) I still have access to the very same data, in the very same interface. Everything just works, no matter where you go.
The release of Google Chrome shows how important the concept is to Google. They are now developing a browser that works better with web-based applications. Mozilla has also taken a stab at this technology with WebRunner/Prism. Adobe has been working in the arena with Adobe Air.
As systems progress and we continue to see items that are mobile-centric (like the netbooks, iPhones, etc) this technology will progress. We will continue to move our storage off our of system hard-drives and into data centers.
I encourage everyone to try out some ASPs, and write back with your favorites.
Having the ability to go from one location/workstation to another, while still having access to your data, is an important hurdle to jump. Many business tackle this issue with "roaming profiles" and other shared resources. But what do you at home do when sharing a profile between, home, work, friends, and the library isn't an option? I'd assume you use an Application Service Provider.
Application Service Providers aren't any new concept, and Google is far from the first Company in invest time, money, and resources into the idea.
From Wikipedia: "In terms of their common goal of enabling customers to outsource specific computer applications so they can focus on their core competencies, ASPs may be regarded as the indirect descendants of the service bureaus of the 1960s and 1970s. In turn, those bureaus were trying to fulfill the vision of computing as a utility, which was first proposed by John McCarthy in a speech at MIT in 1961."
The idea is simple, you register for a service/application that is provided online. All of your information/data is stored on the providers servers. When you need to access the service/data you simple visit the website, and login, no matter your location.
I personally rely on cloud-based services as much as I rely on mobile applications. I have almost all of my email in Google's Gmail (either directly or through POP support or forwarding). I use the Google Calendar on a daily bases to help keep me on track, and update others of my whereabouts (when needed). Google Reader is a dream-come-true - one of the best readers available. Even this blog is an example of a Cloud based service I use. My list could continue, just as I am sure yours could. Even social-networks are a form of cloud computing.
I can easily go from my laptop at the airport, to the desktop at my house and never miss an article, re-read an email, or forget about an appointment. But better yet, when I am in an unfamiliar place (the library, public system, friends house) I still have access to the very same data, in the very same interface. Everything just works, no matter where you go.
The release of Google Chrome shows how important the concept is to Google. They are now developing a browser that works better with web-based applications. Mozilla has also taken a stab at this technology with WebRunner/Prism. Adobe has been working in the arena with Adobe Air.
As systems progress and we continue to see items that are mobile-centric (like the netbooks, iPhones, etc) this technology will progress. We will continue to move our storage off our of system hard-drives and into data centers.
I encourage everyone to try out some ASPs, and write back with your favorites.
Saturday, September 6, 2008
AdSense
Some of you may have noticed a PSA (Public Service Announcement) Ad on the side of the blog, as well as a large amount of space under each post. Both of these should be filled with normal AdSense ads. However, do to some account issue they were not (lost the PIN, etc).
I have corrected all of the account issues, so you should start to see Ads soon. The ads are used simply to fund the webserver etc. I've never made even enough to do that, so in no way am I making a profit.
Look forward to some good articles soon. They are on the way.
I have corrected all of the account issues, so you should start to see Ads soon. The ads are used simply to fund the webserver etc. I've never made even enough to do that, so in no way am I making a profit.
Look forward to some good articles soon. They are on the way.
Friday, August 29, 2008
Still Blogging
Evening,
I wanted to let everyone know I am still blogging! In fact I have two articles that I am in the process of developing and performing further research. I hope to have them published soon (in the next few days).
Sent via BlackBerry
Mobility
No, not the commercial about powered-scooters, but the ability to roam freely and still have access to all of your data. Mobility has become a growing trend, more and more websites focus heavily on mobile interfaces and applications, to ensure their user-base has access to the services provided, no matter their location.
I thought it would be fitting to type this blog entry on my Blackberry, the irony would have been warranted. However, due to still owning a 8700c, I do not have the ability to spell-check my emails (and I am a horrid speller). Although with the ability to post blog entries via email (through blogger), I most certainly could have done so.
A few years ago there was a big movement to enable websites to be compatible on cell-phones and develop mobile related applications. I will not lie, I was a non-believer. I didn't see the average person (even technical savvy ones) using their phone to browse the web.
Download speeds were horrible, and the content layout (on a tiny screen) almost unbearable. Combine these issues with high data prices, I saw the technology going no where fast! But then something interesting happened, smart phones became common ground.
No longer did you see only business executives and rich kids running around the streets with a "smart phones". These devices commonly tote QWERTY (Full) keyboards and a larger screen. The sole purpose of the device is to provide more features then just a "phone".
Now you had a small computer in your pocket. Replacing the old PDA with something that makes phone calls as well. You were walking around with a contact list, calendar, phone, and more, on one device. But best of all you had a web-browser.
All of the WAP enabled websites were easily accessible on a easy to use device, where ever you would go. At this point I jumped on the "band-wagon". I purchased a Blackberry. To be honest, my addition to the (sometimes referred to CrackBerry) device, has only grown stronger as time progresses.
I original used the device solely for email and appointments. Having the ability to keep in touch with clients, family, and friends was always helpful. But I also had an entire archive of my data. Anytime I would need to look something up, or recall a conversation, a quick search and I had the email.
From there I installed amazing apps such as, Opera Mini, Google Maps, TwitterBerry, Beyond411 and plenty more. I truly live a mobile life.
I spend the majority of my life away from the desk, and therefore away from the desktop. That is precisely the reason I own a "desktop-replacement" (overly powerful/slightly heave laptop). But when I am driving down the highway, booting my laptop and catching some WiFi isn't an option. Luckily I have the mobile market to turn to and trust.
With the release of the iPhone and the anticipated release of the Android platform, the experience is only getting better. More and more applications are released, and more and more services are being available each day.
If you haven't taken the plunge into the mobile market, now is the time to do so. The desktop computer will never be replaced, but in five years, you will most definitely have everything you need, in your pocket/hand.
I thought it would be fitting to type this blog entry on my Blackberry, the irony would have been warranted. However, due to still owning a 8700c, I do not have the ability to spell-check my emails (and I am a horrid speller). Although with the ability to post blog entries via email (through blogger), I most certainly could have done so.
A few years ago there was a big movement to enable websites to be compatible on cell-phones and develop mobile related applications. I will not lie, I was a non-believer. I didn't see the average person (even technical savvy ones) using their phone to browse the web.
Download speeds were horrible, and the content layout (on a tiny screen) almost unbearable. Combine these issues with high data prices, I saw the technology going no where fast! But then something interesting happened, smart phones became common ground.
No longer did you see only business executives and rich kids running around the streets with a "smart phones". These devices commonly tote QWERTY (Full) keyboards and a larger screen. The sole purpose of the device is to provide more features then just a "phone".
Now you had a small computer in your pocket. Replacing the old PDA with something that makes phone calls as well. You were walking around with a contact list, calendar, phone, and more, on one device. But best of all you had a web-browser.
All of the WAP enabled websites were easily accessible on a easy to use device, where ever you would go. At this point I jumped on the "band-wagon". I purchased a Blackberry. To be honest, my addition to the (sometimes referred to CrackBerry) device, has only grown stronger as time progresses.
I original used the device solely for email and appointments. Having the ability to keep in touch with clients, family, and friends was always helpful. But I also had an entire archive of my data. Anytime I would need to look something up, or recall a conversation, a quick search and I had the email.
From there I installed amazing apps such as, Opera Mini, Google Maps, TwitterBerry, Beyond411 and plenty more. I truly live a mobile life.
I spend the majority of my life away from the desk, and therefore away from the desktop. That is precisely the reason I own a "desktop-replacement" (overly powerful/slightly heave laptop). But when I am driving down the highway, booting my laptop and catching some WiFi isn't an option. Luckily I have the mobile market to turn to and trust.
With the release of the iPhone and the anticipated release of the Android platform, the experience is only getting better. More and more applications are released, and more and more services are being available each day.
If you haven't taken the plunge into the mobile market, now is the time to do so. The desktop computer will never be replaced, but in five years, you will most definitely have everything you need, in your pocket/hand.
Audio. Video. Data. AWIS.
Wanted to inform everyone of a new project I am working on.
You may have read a tweet of mine, noticed a news article, or spotted a forum post, but for now the details are staying secretive.
I posted a nice teaser on the project homepage: Project AWIS
Stay tuned for more information as we get closer to a "release" date.
You may have read a tweet of mine, noticed a news article, or spotted a forum post, but for now the details are staying secretive.
I posted a nice teaser on the project homepage: Project AWIS
Stay tuned for more information as we get closer to a "release" date.
Thursday, August 28, 2008
XP AntiVirus 2008 Fun...Not
Many of you have more then likely heard about the newest wave of malware, XP AntiVirus 2008, 2009, or the other list of names they are toting now. For those of you who have, skip below to the "story", for the rest, continue, and I'll briefly describe the newest trendy threat.
Threat:
Over the past few months large-scale web-defacement sprees have been compromising legitimate (popular) websites and injecting a whole slew of malicious code. Big-name sites once compromised, would deliver malware directly to the unsuspecting users who visited the site. With trust on the malware distributors side, many users would ignore the typical security precautions.
As this practice became more wide-spread the malware became a bit more "realistic" and "authentic" looking. The attacks turned from the typical "mysterious" files being pushed to the system, to an elaborate social-engineering workshop.
New malware is being developed that looks and functions much like real software. The first to hit the circuits was XP AntiVirus. The malware looks and functions exactly like real Anti Virus software, however in the background it is stealing all of your personal information (passwords, financial information, etc, etc).
Users would visit a legitamet (and trusted) website, which would inform them that "XP" had released an update to their AV product. Knowing they were on a popular, trusted site, they would then click "Ok", download the software and become infected.
Screenshots:

The Background:
My mother owns a number of computers, ranging from personal servers (that I have setup) to a few laptops. She runs Linux on everything, not by choice, simply because I force her to. I don't mean to sound harsh about it, but Linux doesn't suffer from half of the problems Windows does. And that is even more true with someone like your mother (who is more then likely not computer savvy).
However, I lied a bit, she does own and use one Windows-based laptop. Only one, every other component runs Linux (even the router). She refuses to give up this system, at all costs. Mainly due to a few very Linux-unfriendly websites and my lack of time to help get them working.
Of course this one Windows system is the one I receive the most "calls" about. Nothing is every working correctly, and every time I touch the thing there is another piece of spyware.
So after this last "rebuild" of the system I locked things down really well. To the point she was annoyed at the lack of usability. Unfortunately I made the mistake of locking the system down from external "unwanted" penetration. I didn't put much protection in place from the user. I assumed all of the "awareness" would work, and the system would stay in a fairly clean state.
Don't misunderstand, there were security applications, that prompted her when malice actions may be present (even if she was the one who started them), but lets face it, everyone clicks "Allow" anyway.
The Problem:
I was partially correct, the "awareness" did work, she herself did not infect her system with anything. But my brother did.
She was out of the house, and he "snuck" onto the system (which just-so-happened to be mistakenly unlocked). He downloaded the XPAV software to his PSP (Portable Playstation) and then transferred it to the laptop. He then installed the application (or should we now call it malware). Allowed all web-updates and downloads of further trojans. And then denied the entire thing.
The Solution:
This malware is changing everyday, and each infection is different. The malware downloads a number of additional malice components, and most is undetectable by current signatures.
So a complete re-install of Windows, and a lot of yelling was in order.
The Lesson:
Of course you have heard this before, and I can assure you, you will hear it again. The user is always the weakest link, and no matter how secure the system is, you have to educate the users. And protect yourself against them.
Also, don't just educate the primary user, stress the issues to anyone who may come in contact the system.
Oh - and lock your screen when you walk away.
More information of the malware can be found: here, here, or here.
Threat:
Over the past few months large-scale web-defacement sprees have been compromising legitimate (popular) websites and injecting a whole slew of malicious code. Big-name sites once compromised, would deliver malware directly to the unsuspecting users who visited the site. With trust on the malware distributors side, many users would ignore the typical security precautions.
As this practice became more wide-spread the malware became a bit more "realistic" and "authentic" looking. The attacks turned from the typical "mysterious" files being pushed to the system, to an elaborate social-engineering workshop.
New malware is being developed that looks and functions much like real software. The first to hit the circuits was XP AntiVirus. The malware looks and functions exactly like real Anti Virus software, however in the background it is stealing all of your personal information (passwords, financial information, etc, etc).
Users would visit a legitamet (and trusted) website, which would inform them that "XP" had released an update to their AV product. Knowing they were on a popular, trusted site, they would then click "Ok", download the software and become infected.
Screenshots:

The Background:
My mother owns a number of computers, ranging from personal servers (that I have setup) to a few laptops. She runs Linux on everything, not by choice, simply because I force her to. I don't mean to sound harsh about it, but Linux doesn't suffer from half of the problems Windows does. And that is even more true with someone like your mother (who is more then likely not computer savvy).
However, I lied a bit, she does own and use one Windows-based laptop. Only one, every other component runs Linux (even the router). She refuses to give up this system, at all costs. Mainly due to a few very Linux-unfriendly websites and my lack of time to help get them working.
Of course this one Windows system is the one I receive the most "calls" about. Nothing is every working correctly, and every time I touch the thing there is another piece of spyware.
So after this last "rebuild" of the system I locked things down really well. To the point she was annoyed at the lack of usability. Unfortunately I made the mistake of locking the system down from external "unwanted" penetration. I didn't put much protection in place from the user. I assumed all of the "awareness" would work, and the system would stay in a fairly clean state.
Don't misunderstand, there were security applications, that prompted her when malice actions may be present (even if she was the one who started them), but lets face it, everyone clicks "Allow" anyway.
The Problem:
I was partially correct, the "awareness" did work, she herself did not infect her system with anything. But my brother did.
She was out of the house, and he "snuck" onto the system (which just-so-happened to be mistakenly unlocked). He downloaded the XPAV software to his PSP (Portable Playstation) and then transferred it to the laptop. He then installed the application (or should we now call it malware). Allowed all web-updates and downloads of further trojans. And then denied the entire thing.
The Solution:
This malware is changing everyday, and each infection is different. The malware downloads a number of additional malice components, and most is undetectable by current signatures.
So a complete re-install of Windows, and a lot of yelling was in order.
The Lesson:
Of course you have heard this before, and I can assure you, you will hear it again. The user is always the weakest link, and no matter how secure the system is, you have to educate the users. And protect yourself against them.
Also, don't just educate the primary user, stress the issues to anyone who may come in contact the system.
Oh - and lock your screen when you walk away.
More information of the malware can be found: here, here, or here.
Back...Again..Maybe?
Hello (yet again),
Well you can't say that I didn't warn you! And we all know that past actions predict future actions. You should have known the whole "blogging" thing wasn't going to work.
Yet, here I am sitting behind the keyboard, writing another post. I miss the "idea" of blogging, not the actual process. It truly isn't that I do not like blogging, because I do. I just can't seems to remember (or better yet fit the time into my day). But, I am going to work on that.
As of recent I have found the time to fit Twitter into my life. If I can post tweets, I can certainly post a few blurbs on a blog, right?
So expect some posts soon, or don't -- either way I am back for a bit...
Well you can't say that I didn't warn you! And we all know that past actions predict future actions. You should have known the whole "blogging" thing wasn't going to work.
Yet, here I am sitting behind the keyboard, writing another post. I miss the "idea" of blogging, not the actual process. It truly isn't that I do not like blogging, because I do. I just can't seems to remember (or better yet fit the time into my day). But, I am going to work on that.
As of recent I have found the time to fit Twitter into my life. If I can post tweets, I can certainly post a few blurbs on a blog, right?
So expect some posts soon, or don't -- either way I am back for a bit...
Monday, March 3, 2008
Capture the Flag: Towson and CCBC - Just for fun
Saturday, March 1st, from 9:30am to around 4:00pm (EST) both the Community College of Baltimore County and Towson University participated in a Capture the Flag event. Although a winner was announced the event was just for fun, and an attempt to gear students up for the upcoming Collegiate Cyber Defense Competition, and by upcoming, I mean next weekend. But more on the competition later...
The event was hosted by Towson, setup in complete by Dr. Michael O'Leary team-mates mixed amongst each others. This allowed for the entire events to be . The event was run much like a typical capture the flag, with each group attempting to both defend their own systems, while attacking the other group. The groups were derived from a "dodge-ball" style pick, leaving the CCBC and Towson teammates mixed amongst each other. Causing the entire event to be rather layed back, taking the secrecy and pressure off the majority of the students.
I was selected as one of the team-captains and was able to pick a rather good team. But overall I had rather little interaction with anyone on my team - this was done on purpose and part of a well thought-out strategy. I work on the offensive-side almost exclusively, only answering questions for the defensive counter-parts on my team. I was the only one running offense for our team. I'll do my best to describe the event after the jump, keep in mind though, I did little defensively.
The Setup: Each group had five or six students, and was allowed a "team name." Each group had an identical setup, excluding the system host names and the IP addresses. The systems included a mixture of Windows and Suse installations, with a varying degree of patch levels. In addition to the unknown "base-line" security, each system was pre-configured with a handful of holes.
The Injects: Much like the CCDC, this event would not be complete without "business injects." I have a feeling this type of caveat will be all to common in CTF events world-wide with time. Although I did no defense, I did over hear a few of the injects, seems they ranged from, Determine the IP address of every web server to setting up a fully functionally syslog server with every system logging.
The Scoring: Scoring was based on both offense and defense. A team who successfully found a security hole (one of the ones placed on the system at the start of the event) gained points. If they secured the same vulnerability, they scored. And (my part) if they exploited the vulnerability against the other team, they yet again scored. In addition, any exploitation resulted in some points, and becoming administrator/root, resulted in a higher point reward. As well as thwarting an intrusion, netted some points. One more score vector that I thought was a good add was something Dr Leary called "style." Anytime you did something "out-of-the-box," clever or just plain 1337, your team found its self a few points further.
The Recon: I approached the days event much like a blind pen-test. I truly only knew a few things walking-in-the-door, and only a few more things were explained before we started. At the beginning of the event I knew the following:
The Attacks (10.0.1.23): Within the first ten minuets of the events I had already obtained administrative access to two systems, and had setup some ways to maintain access. The first system I attacked was a Windows 2000 system. Exploiting the lsass vulnerability using metasploit, I obtained a reverse shell. With time on my side (knowing they had most likely not thoroughly check the system) I immediately added an account named "root" and added it to the "Domain Admins" group, followed by changing the administrator password. Next I looked around the system, and found a internal employee "phone directory" which I promptly moved to my system. This landed our team a good amount of points up front.
The Attacks (10.0.1.26): This is a really good story, and a lot less technical. This was the second box I attacked within the first ten minuets. I more or less completed the same tasks as above on this system, which was also a Windows 2000 installation. The part worth mentioning however, was this was our teams system. Turns out, unbeknownced to me, one of our systems was having network issues at the start of the event, and they failed to give me this address. I completely "owned" one of my own systems. I then promptly reverted my changes back, and moved along.
The Attacks (10.0.1.24): The system (Windows 2000) has VNC setup, with no password. I jumped on, changed the Administrator password, started to add a few users. And noticed Back Orifice was installed, so I started setting it up, but was promptly caught. Seems they made a mistake similar to mine. They VNC'ed into their own system, and thought they were in one of our systems. This accounted for the mouse moving. Dr O'Learly came to "score the breach" and informed them that they were on their system. Puzzled, they then fluttered to find out who was really on the system and setting up Back Orifice. Sitting on the box, they relized they were being attacked, and attempted to close my windows, which I just reopened. Then they attempted to shutdown the box, which I canceled, then they pulled the plug. Oh well, they still had to reset the password.
Guest SSH: One of the injects was to setup SSH on every system with a guest account. This more or less meant game-over. I used this to leverage further access for the remainder of the event.
(The rest of the attacks are not listed in any particular order. Nor are not the only attacks that were preformed, just the ones I have notes written for...)
The Attacks (10.0.1.38): This was a Linux server, running http, ftp, and a few other services. The /etc/passwd file was set world-writable, so I changed the guest account to have a uid of 0, and changed the password. I then re-logged in, change the root password. Grabbed the shadow file, and began cracking the other user-account passwords. In attempt to maintain access I then grabbed a copy of the root ssh private key. For an added bonus, I changed the daemon account to uid 0. I trojaned su and ssh on the spot, with a quick bash script that would send me a copy of the password, I also redirected the root bash history to myself. I defaced the website, with something childish.
The Attacks (10.0.1.37): Just defaced the website, world-readable, nothing special.
The Attacks (10.0.1.41): This Linux server contained a ecommerce website. The database password was stored in a world-readable include file, giving me access to the database. I was then able to obtain customer information, including credit-card numbers (every time I say this people ask if they were real...um...yeah...no). I was also able to add myself as an administrator on the site. I then defaced the site (Changed all of the "Road-Runner" pictures to Bugs Bunny) and then for fun played around with some SQL injections.
The Attacks (10.0.1.42): I swear this was a spitting image of the previous box, except it was a "bank" and contained bank information. And I deleted the bank instead of defacing it.
Defacements: Every time they reverted a site, I more or less changed it back. I erased key files (after "I" backed them up) and they then started to just leave comments, like "Stay Out". Or "You don't belong here". So I started leaving comments back like "Nor Do You", or "Nice Bank". The defacement became a ranting board between me and the other group, quite fun actually. One more note to add, I added a phpinfo() to most of the sites, just for fun.
Fork Bombs: Near the end of the event I became bored, and decided to just start messing with the systems. Deciding not to just rf -Rf / I started to fork bomb every system.
Filling The Disk: At the same time I was fork bombing the systems, I decided it would be fun to fill the hard-drives. So I wrote a few scripts that starting to fill the hard drive. At the end of the event, all of the Linux systems were between 80-90% filled. If we had a bit more time, they would have had a good amount of issues...
Syslog: At the ten minuets to the end of the event, both teams successfully rooted each others syslog server.
The Winner: Seems the best defense is a good offense. My team won, by a few hundred points.
That about wraps up the events, drop any questions in the comments. Look for a post on the results of the competition, during and after next weekend. Also take a look at the Interesting News Feed.
The event was hosted by Towson, setup in complete by Dr. Michael O'Leary team-mates mixed amongst each others. This allowed for the entire events to be . The event was run much like a typical capture the flag, with each group attempting to both defend their own systems, while attacking the other group. The groups were derived from a "dodge-ball" style pick, leaving the CCBC and Towson teammates mixed amongst each other. Causing the entire event to be rather layed back, taking the secrecy and pressure off the majority of the students.
I was selected as one of the team-captains and was able to pick a rather good team. But overall I had rather little interaction with anyone on my team - this was done on purpose and part of a well thought-out strategy. I work on the offensive-side almost exclusively, only answering questions for the defensive counter-parts on my team. I was the only one running offense for our team. I'll do my best to describe the event after the jump, keep in mind though, I did little defensively.
The Setup: Each group had five or six students, and was allowed a "team name." Each group had an identical setup, excluding the system host names and the IP addresses. The systems included a mixture of Windows and Suse installations, with a varying degree of patch levels. In addition to the unknown "base-line" security, each system was pre-configured with a handful of holes.
The Injects: Much like the CCDC, this event would not be complete without "business injects." I have a feeling this type of caveat will be all to common in CTF events world-wide with time. Although I did no defense, I did over hear a few of the injects, seems they ranged from, Determine the IP address of every web server to setting up a fully functionally syslog server with every system logging.
The Scoring: Scoring was based on both offense and defense. A team who successfully found a security hole (one of the ones placed on the system at the start of the event) gained points. If they secured the same vulnerability, they scored. And (my part) if they exploited the vulnerability against the other team, they yet again scored. In addition, any exploitation resulted in some points, and becoming administrator/root, resulted in a higher point reward. As well as thwarting an intrusion, netted some points. One more score vector that I thought was a good add was something Dr Leary called "style." Anytime you did something "out-of-the-box," clever or just plain 1337, your team found its self a few points further.
The Recon: I approached the days event much like a blind pen-test. I truly only knew a few things walking-in-the-door, and only a few more things were explained before we started. At the beginning of the event I knew the following:
- I had two "attack boxes" with BackTrack (version 2) installed
- I was on the same addresses space as the other team (although that was all I knew)
- The systems had Windows or Linux installed
- No physically devices (printers, routers, etc) were involved
- I couldn't attack core network resources (class equipments; servers, hosts, etc)
- One of my team-mates had a "magically" piece of paper that contained all of our "system" hostnames, usernames, passwords, and OS.
The Attacks (10.0.1.23): Within the first ten minuets of the events I had already obtained administrative access to two systems, and had setup some ways to maintain access. The first system I attacked was a Windows 2000 system. Exploiting the lsass vulnerability using metasploit, I obtained a reverse shell. With time on my side (knowing they had most likely not thoroughly check the system) I immediately added an account named "root" and added it to the "Domain Admins" group, followed by changing the administrator password. Next I looked around the system, and found a internal employee "phone directory" which I promptly moved to my system. This landed our team a good amount of points up front.
The Attacks (10.0.1.26): This is a really good story, and a lot less technical. This was the second box I attacked within the first ten minuets. I more or less completed the same tasks as above on this system, which was also a Windows 2000 installation. The part worth mentioning however, was this was our teams system. Turns out, unbeknownced to me, one of our systems was having network issues at the start of the event, and they failed to give me this address. I completely "owned" one of my own systems. I then promptly reverted my changes back, and moved along.
The Attacks (10.0.1.24): The system (Windows 2000) has VNC setup, with no password. I jumped on, changed the Administrator password, started to add a few users. And noticed Back Orifice was installed, so I started setting it up, but was promptly caught. Seems they made a mistake similar to mine. They VNC'ed into their own system, and thought they were in one of our systems. This accounted for the mouse moving. Dr O'Learly came to "score the breach" and informed them that they were on their system. Puzzled, they then fluttered to find out who was really on the system and setting up Back Orifice. Sitting on the box, they relized they were being attacked, and attempted to close my windows, which I just reopened. Then they attempted to shutdown the box, which I canceled, then they pulled the plug. Oh well, they still had to reset the password.
Guest SSH: One of the injects was to setup SSH on every system with a guest account. This more or less meant game-over. I used this to leverage further access for the remainder of the event.
(The rest of the attacks are not listed in any particular order. Nor are not the only attacks that were preformed, just the ones I have notes written for...)
The Attacks (10.0.1.38): This was a Linux server, running http, ftp, and a few other services. The /etc/passwd file was set world-writable, so I changed the guest account to have a uid of 0, and changed the password. I then re-logged in, change the root password. Grabbed the shadow file, and began cracking the other user-account passwords. In attempt to maintain access I then grabbed a copy of the root ssh private key. For an added bonus, I changed the daemon account to uid 0. I trojaned su and ssh on the spot, with a quick bash script that would send me a copy of the password, I also redirected the root bash history to myself. I defaced the website, with something childish.
The Attacks (10.0.1.37): Just defaced the website, world-readable, nothing special.
The Attacks (10.0.1.41): This Linux server contained a ecommerce website. The database password was stored in a world-readable include file, giving me access to the database. I was then able to obtain customer information, including credit-card numbers (every time I say this people ask if they were real...um...yeah...no). I was also able to add myself as an administrator on the site. I then defaced the site (Changed all of the "Road-Runner" pictures to Bugs Bunny) and then for fun played around with some SQL injections.
The Attacks (10.0.1.42): I swear this was a spitting image of the previous box, except it was a "bank" and contained bank information. And I deleted the bank instead of defacing it.
Defacements: Every time they reverted a site, I more or less changed it back. I erased key files (after "I" backed them up) and they then started to just leave comments, like "Stay Out". Or "You don't belong here". So I started leaving comments back like "Nor Do You", or "Nice Bank". The defacement became a ranting board between me and the other group, quite fun actually. One more note to add, I added a phpinfo() to most of the sites, just for fun.
Fork Bombs: Near the end of the event I became bored, and decided to just start messing with the systems. Deciding not to just rf -Rf / I started to fork bomb every system.
Filling The Disk: At the same time I was fork bombing the systems, I decided it would be fun to fill the hard-drives. So I wrote a few scripts that starting to fill the hard drive. At the end of the event, all of the Linux systems were between 80-90% filled. If we had a bit more time, they would have had a good amount of issues...
Syslog: At the ten minuets to the end of the event, both teams successfully rooted each others syslog server.
The Winner: Seems the best defense is a good offense. My team won, by a few hundred points.
That about wraps up the events, drop any questions in the comments. Look for a post on the results of the competition, during and after next weekend. Also take a look at the Interesting News Feed.
Saturday, March 1, 2008
Apple Sued Over iPhone Caller ID - Lawyer Taglines
The Article: Apple Sued Over iPhone Caller ID
The Summary: The Apple iPhone has a "two-line LCD" caller-id function, that [oh-my] tells you who is calling. Seems "Romek Figa" owns a patent for such a feature. Figa is attempting to have Apple pay damages and license the feature. Apple thus far is refusing thus the impending lawsuit. Seems other major phone companies have already abided by Figa's rules, but he hasn't chosen to go through the proper channels at Apple.
Comments: I really want to take this article in an entierly diffrent direction, but before I do so, I'll comment on the article. I don't have the patent information in front of me, so I am skeptical to the entire idea someone whos a patent on such a wide-spread feature. But I've seen worse patents, (the mouse?). Eitherway I'll point you to this other article I added to my feed: Patents, Copyrights, Trademarsk, Oh My!
Now, for the spin, and the true point of this post. If you look at the article you'll see an ever common tagline, although this one is funnier then most. " Disclaimer: Nilay is a lawyer, but he's not your lawyer, and none of this is legal advice or analysis." I laugh aloud everytime I read one of these. It reminds me of the "warning" on coffee (May Be Hot), or the cautions on strollers (Remove Child Before Closing). Are people really that dumb? Or wrose are they really that sue happy -- looking at the context of the article, I guess so. But do we now need to write a disclaimer each time we give our opinion based on a job title? Leave your thoughts in the comment section...
Disclaimer: Justin is a guy who is attempting to write a blog, but he doesn't write your blog. Anything within his blog should be consiered his own opinion and now yours. Unless it is your opinion too.
The Summary: The Apple iPhone has a "two-line LCD" caller-id function, that [oh-my] tells you who is calling. Seems "Romek Figa" owns a patent for such a feature. Figa is attempting to have Apple pay damages and license the feature. Apple thus far is refusing thus the impending lawsuit. Seems other major phone companies have already abided by Figa's rules, but he hasn't chosen to go through the proper channels at Apple.
Comments: I really want to take this article in an entierly diffrent direction, but before I do so, I'll comment on the article. I don't have the patent information in front of me, so I am skeptical to the entire idea someone whos a patent on such a wide-spread feature. But I've seen worse patents, (the mouse?). Eitherway I'll point you to this other article I added to my feed: Patents, Copyrights, Trademarsk, Oh My!
Now, for the spin, and the true point of this post. If you look at the article you'll see an ever common tagline, although this one is funnier then most. " Disclaimer: Nilay is a lawyer, but he's not your lawyer, and none of this is legal advice or analysis." I laugh aloud everytime I read one of these. It reminds me of the "warning" on coffee (May Be Hot), or the cautions on strollers (Remove Child Before Closing). Are people really that dumb? Or wrose are they really that sue happy -- looking at the context of the article, I guess so. But do we now need to write a disclaimer each time we give our opinion based on a job title? Leave your thoughts in the comment section...
Disclaimer: Justin is a guy who is attempting to write a blog, but he doesn't write your blog. Anything within his blog should be consiered his own opinion and now yours. Unless it is your opinion too.
Wednesday, February 27, 2008
The Laws of Full Disclosure
I added a really interesting article (from Security Focus) to my Interesting News feed. If you are new to my Blog or News Feed, please check it out. I add stories/content I find interesting.
The Article: The Laws of Full Disclosure
Summary: A Security Focus contributor researches the legality of disclosing vulnerability information to the public in twelve European countries.
Comments: This article causes me great concern. I find it absurd that in the year 2008, with the average person starting to think about security, that we would be limiting research. Obviously the only way to secure software is to test it, and then release the information you find. If they disallow people to disclose the information the vendor may never know about the issue, let alone fix it! If they do allow disclosure to the vendor but not the public, then you fall in the issue with vendors ignoring security concerns. Or worse the users never knowing their at risk. Reasonable Disclosure verse Full [Public] Disclosure have been a debate of the security community for all of time, and both have a time and place, but out right criminalizing disclosure and research is insane. I really hope these laws are reviewed.
Leave your comments in the comment section, and if you feel so inclined (and live in one of these areas, contact your government and let them know your concerns).
The Article: The Laws of Full Disclosure
Summary: A Security Focus contributor researches the legality of disclosing vulnerability information to the public in twelve European countries.
- Belgium - Illegal with Conditions - Full Disclosure of vulnerability information is proved to have causes harm to the vendor, is proved to be written for the sole purpose of an intrusion (hacking), or is proved to have been a breach of a employment contract/non-disclosure agreement.
- Denmark - Illegal with Conditions - If you are an employee or contractor for the software development company, vulnerabilities are considered "trade-secretes". Release details instructions to exploit the vulnerability can be considered "assisting in a crime." A competing software company would be fined for release such information.
- Finland - Proof of Concept Illegal with Conditions - Concept code can only be prepared for a CERT.
- France - Mostly Legal - Only illegal when you use the attack or share confidential/proprietary information.
- Germany - Legal
- Greece - Legal
- Hungary - Legal with Conditions - If the information you release is incorrect you can be held liable for damages. It cannot violate patent of copyright clauses.
- Ireland - No Laws - Having "tools" that can result in an intrusion could be a crime, but disclosing vulnerabilities is an uncharted area.
- Italy - Legal with Conditions - You can not decompile code, unless working on interoperability.
- Poland - Legal
- Romania - Illegal with Conditions - If the information is used in an intrusion. In addition writing exploit code is illegal.
- UK - Legal
Comments: This article causes me great concern. I find it absurd that in the year 2008, with the average person starting to think about security, that we would be limiting research. Obviously the only way to secure software is to test it, and then release the information you find. If they disallow people to disclose the information the vendor may never know about the issue, let alone fix it! If they do allow disclosure to the vendor but not the public, then you fall in the issue with vendors ignoring security concerns. Or worse the users never knowing their at risk. Reasonable Disclosure verse Full [Public] Disclosure have been a debate of the security community for all of time, and both have a time and place, but out right criminalizing disclosure and research is insane. I really hope these laws are reviewed.
Leave your comments in the comment section, and if you feel so inclined (and live in one of these areas, contact your government and let them know your concerns).
Google Reader and Intresting News
Get all your news and blogs in one place with Google Reader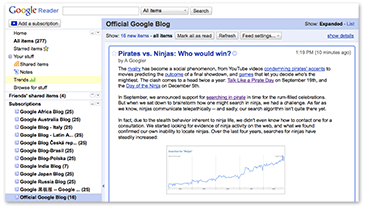
| |
|
I started using Google Reader over a week ago. I more of less grew tired of re-adding all of my "feeds" to each "feedreader" I sit in front of, or re-emailing myself my OPML file each time I make a change. An online reader seemed to be a happy solution to this problem. Allowing me to view all of my news feeds, no matter where I am (even on my Blackberry).
There are a handful of them out there, and in the past I have used a few others. But this was the first time I really made an honest attempt. And Google takes the cake (in my opinion). I highly suggest everyone checks it out.
Here is a list of features I really enjoy:
- Feed Recommendation (At first it was annoying, but as I started "staring" content, it became rather fun to look through the recommendations
- Feed Browsing (You don't even need the RSS URL, you just search for the feed by name, site, content, etc
- Sharing and Staring (You mark content as stared much like emails in Gmail, this allows me to then share the content almost like Digg and other social news sites, the difference I control the content)
- Friends (Allowing you to keep track of news your friends find interesting has really never been easier)
- Trends (Structured Analysis of your News Reading and Feeding activities)
- Offline Mode (Allowing you to view content, without updates/connectivity)
I would also like everyone to check out my "Interesting News Feed" which provides news I find interesting. It is published through Google Reader and includes and RSS feed, in case you want to keep an eye on my findings. In addition, I'll publis blog posts about the really interesting news articles and pass along my two cents.
Interesting News and Feed
Enjoy!
Blogging - Yeah Right!
Hello Universe...
As I stated in my first post (which was published almost a year ago), I not very consistent with blogging.
But, at least I keep trying! So here goes...
As I stated in my first post (which was published almost a year ago), I not very consistent with blogging.
But, at least I keep trying! So here goes...
Subscribe to:
Comments (Atom)